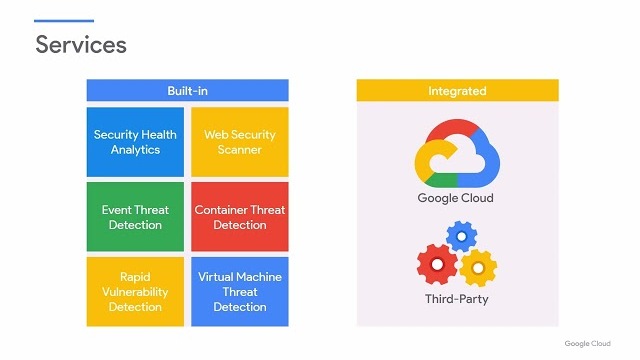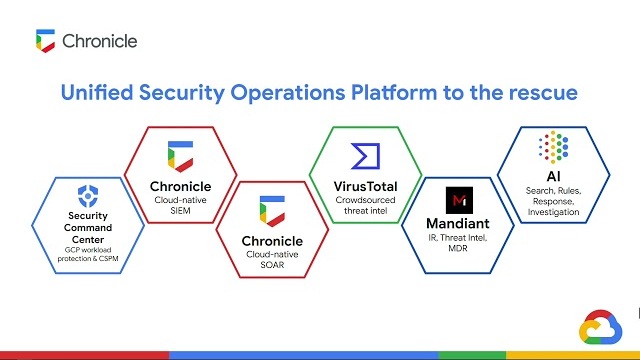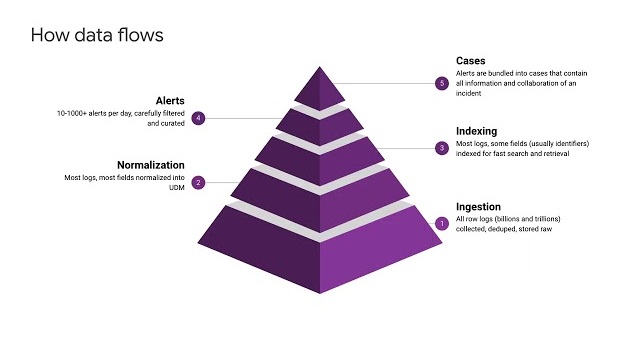
This course provides a comprehensive overview of Google Cloud Security Command Center (SCC) Enterprise, a Cloud-Native Application Protection Platform (CNAPP) solution that helps organizations prevent, detect, and respond to threats across Google Cloud services. You will learn about core SCC...