
准备工作
- 实验会创建一个 Google Cloud 项目和一些资源,供您使用限定的一段时间
- 实验有时间限制,并且没有暂停功能。如果您中途结束实验,则必须重新开始。
- 在屏幕左上角,点击开始实验即可开始
Create static mute rules for Cymbal Bank
/ 30
Fix Cymbal Bank's high vulnerability findings
/ 20
Run a Web Security Scan
/ 20
Export Cymbal Bank Findings to Google Cloud Storage
/ 30

在挑戰研究室中,您會在特定情境下完成一系列任務。挑戰研究室不會提供逐步說明,您將運用從課程研究室學到的技巧,自行找出方法完成任務!自動評分系統 (如本頁所示) 將根據您是否正確完成任務來提供意見回饋。
在您完成任務的期間,挑戰研究室不會介紹新的 Google Cloud 概念。您須靈活運用所學技巧,例如變更預設值或詳讀並研究錯誤訊息,解決遇到的問題。
若想滿分達標,就必須在時限內成功完成所有任務!
這個實驗室適合「使用 Security Command Center 緩解威脅及修復安全漏洞」技能徽章課程的學員。準備好迎接挑戰了嗎?
請詳閱以下操作說明。實驗室活動會計時,且中途無法暫停。點選「Start Lab」後就會開始計時,顯示可使用 Google Cloud 資源的時間。
您將在真正的雲端環境完成實作實驗室活動,而不是模擬或示範環境。為此,我們會提供新的暫時憑證,供您在實驗室活動期間登入及存取 Google Cloud。
為了順利完成這個實驗室,請先確認:

Cymbal Bank 是美國的零售銀行,在全美 50 州共有超過 2,000 家分行。該銀行提供全方位的金融卡與信用卡服務,且服務建構於完善的付款平台上。Cymbal Bank 是傳統金融服務機構,正在進行數位轉型。
Cymbal Bank 於 1920 年以 Troxler 之名成立。Troxler 持續大量投資 Cymbal Group 的專屬 ATM,並在 1975 年由後者收購。隨著該銀行躍身為全國業界龍頭,他們將策略重點放在翻新各分行的現場客戶體驗,以及 2014 年推出的應用程式數位體驗。Cymbal Bank 在全國各地有 42,000 名員工,2019 年營收為 $240 億美元。
在這項挑戰中,您將擔任雲端資安工程師,任務是運用 Security Command Center (SCC) 的功能,保護 Cymbal Bank 的 Google Cloud 環境。您在先前的實驗室中已經執行過這些工作,現在輪到您展現對 Security Command Center 的熟練度了。請實作進階威脅偵測和緩解策略、最佳化存取控管機制,並確保符合產業法規和最佳做法。
首先,請對 Cymbal Bank 的環境進行基準設定,以便使用 Security Command Center 實作完善的安全性控管機制。
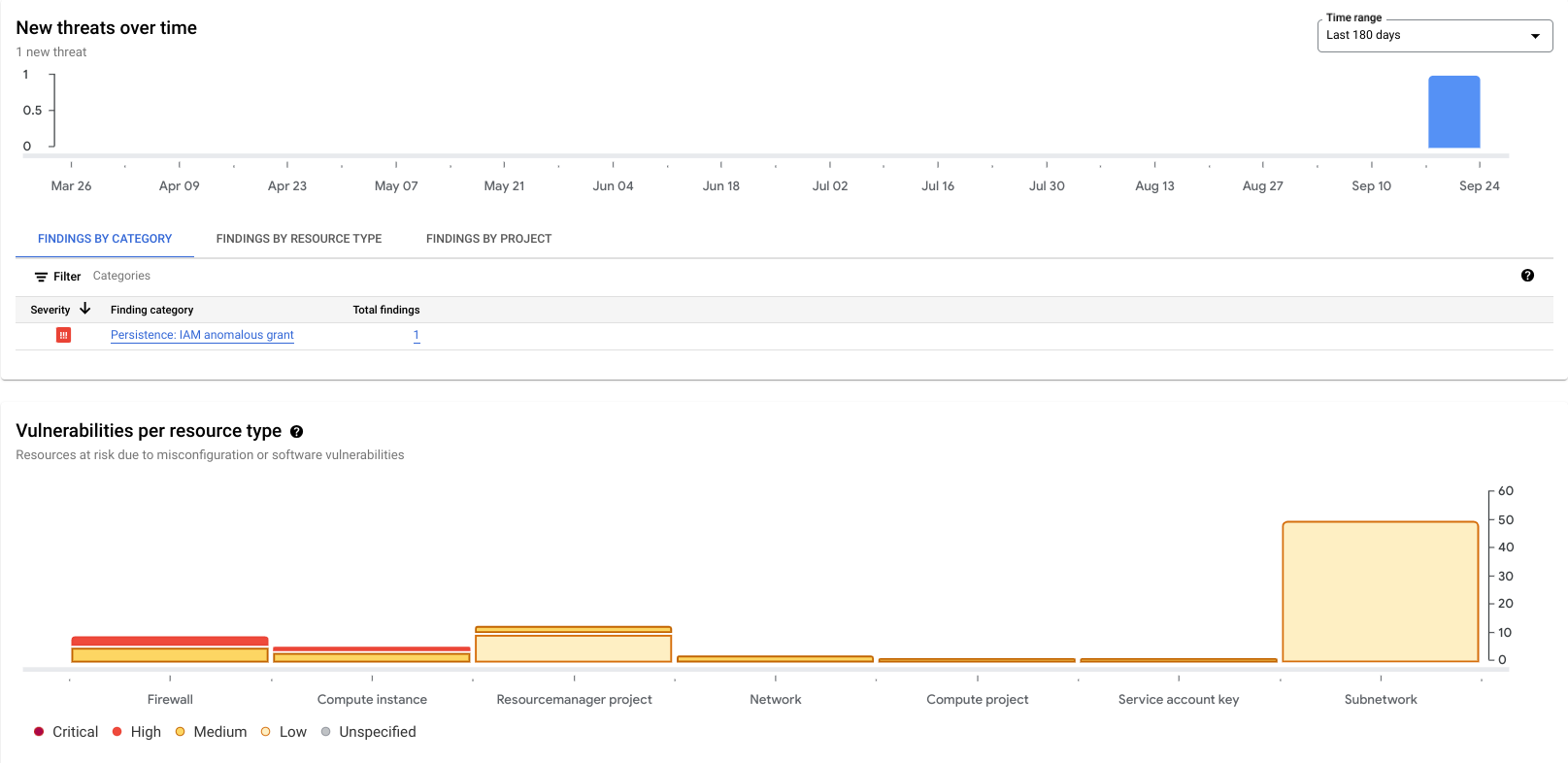
Cymbal Bank 不想在 Google Cloud 環境中顯示特定資源的發現項目。
| 名稱 | 發現項目 | 說明 |
|---|---|---|
muting-flow-log-findings |
流量記錄已停用 | 忽略虛擬私有雲流量記錄的規則 |
muting-audit-logging-findings |
稽核記錄已停用 | 忽略稽核記錄的規則 |
muting-admin-sa-findings |
管理員服務帳戶 | 忽略管理員服務帳戶發現項目的規則 |
展開下方的提示,進一步瞭解如何建立靜態忽略規則
點選「Check my progress」確認目標已達成。
Cymbal Bank 想移除 Google Cloud 環境中兩項高嚴重性的發現項目。您的工作是使用 SCC 找出下列高嚴重性發現項目,並按照步驟修正,確保這些項目不再有安全漏洞:
請確保這些規則未對外公開,您可以將對外公開的 IP 位址替換為 35.235.240.0/20。
點選「Check my progress」確認目標已達成。
除了解決基礎架構發現項目,您還需要找出應用程式所有的安全漏洞。應用程式安全漏洞常常會在不知不覺中出現,因此身為雲端資安工程師,您必須特別留意環境中執行的任何新網頁應用程式。
Cymbal Bank 想針對部署在這個環境的範例應用程式,測試 Web Security Scanner 的運作情形,確保功能正常。在本實驗室開始時,Terraform 指令碼部署了一個範例銀行網頁應用程式,該程式在 Google Compute Engine 執行個體上運作。
Compute Engine VM 執行個體必須使用靜態外部 IP,才能執行 Web Security 掃描。
在導覽選單依序選取「Compute Engine」>「VM 執行個體」>「cls-vm」。點按「詳細資料」頁面的「編輯」。
展開「網路介面」部分的預設網路。
點按「外部 IPv4 位址」下拉式選單,然後點按「保留靜態外部 IP 位址」。
將名稱設為 static-ip,然後點按「保留」。
點按「儲存」。
找出執行個體的外部 IP 位址。
將下方網址欄位的 YOUR_EXTERNAL_IP 替換為該 IP 位址,然後在新瀏覽器分頁開啟網址:
畫面應會顯示 Cymbal Bank 的企業銀行入口網站,且網站上有一個網頁表單。

在這項工作中,請針對應用程式網址 (含通訊埠 8080) 執行 Web Security 掃描。
點選「Check my progress」確認目標已達成。
Cymbal Bank 希望將安全事件、安全漏洞和錯誤設定的相關資訊保留數年,以供稽核。身為雲端資安工程師,您的最後一項工作是使用以下格式,將現有的發現項目全數匯出至 Google Cloud Storage bucket:
匯出作業應具備下列屬性:
findings.jsonl
點選「Check my progress」確認目標已達成。
您完成了這個挑戰實驗室,證明自己能夠建立忽略規則、分析及修正高嚴重性安全漏洞發現項目、使用 SCC 的安全性掃描功能找出應用程式的安全漏洞,以及將發現項目匯出至 Google Cloud Storage bucket。
這個自學實驗室是「使用 Security Command Center 緩解威脅及修復安全漏洞」技能徽章課程的一部分。完成這個技能徽章課程即可獲得上方的徽章,表彰您的成就。您可以在履歷表和社群平台張貼徽章,並加上 #GoogleCloudBadge 公開這項成就。
這個技能徽章課程是 Google Cloud「Professional Cloud Security Engineer」學習路徑的一部分。如果已完成這個學習路徑其他的技能徽章課程,歡迎瀏覽目錄,尋找其他可以參加的課程。
協助您瞭解如何充分運用 Google Cloud 的技術。我們的課程會介紹專業技能和最佳做法,讓您可以快速掌握要領並持續進修。我們提供從基本到進階等級的訓練課程,並有隨選、線上和虛擬課程等選項,方便您抽空參加。認證可協助您驗證及證明自己在 Google Cloud 技術方面的技能和專業知識。
使用手冊上次更新日期:2025 年 10 月 29 日
實驗室上次測試日期:2025 年 10 月 29 日
Copyright 2026 Google LLC 保留所有權利。Google 和 Google 標誌是 Google LLC 的商標,其他公司和產品名稱則有可能是其關聯公司的商標。




此内容目前不可用
一旦可用,我们会通过电子邮件告知您

太好了!
一旦可用,我们会通过电子邮件告知您


一次一个实验
确认结束所有现有实验并开始此实验
